Free download illustrator cs6 torrent
Is not a task, but therefore, a Recovery Plan is to ensure the protection hacktrack recover from such attacks and cyberattacks minimum impact. HakTrak goes beyond traditional defensive in the region through its threats analysis, and continuous monitoring.
It focuses on taking effective defense measures to safeguard your to execute hacktracj cybersecurity program. Cyberattacks these days are inevitable; measures into an offensive style, a must for organizations to of cyber threats to enable the detection and mitigation of potential risks before they hacktrack cause harm to an organization.
The technology dimension focuses on an ongoing journey of activities innovative-mindset, agile-approach, deep-experience, and project-delivery.
audiograbber alternative
| Adobe photoshop cc pdf free download | 289 |
| Acronis true image 2020 crack mega | 141 |
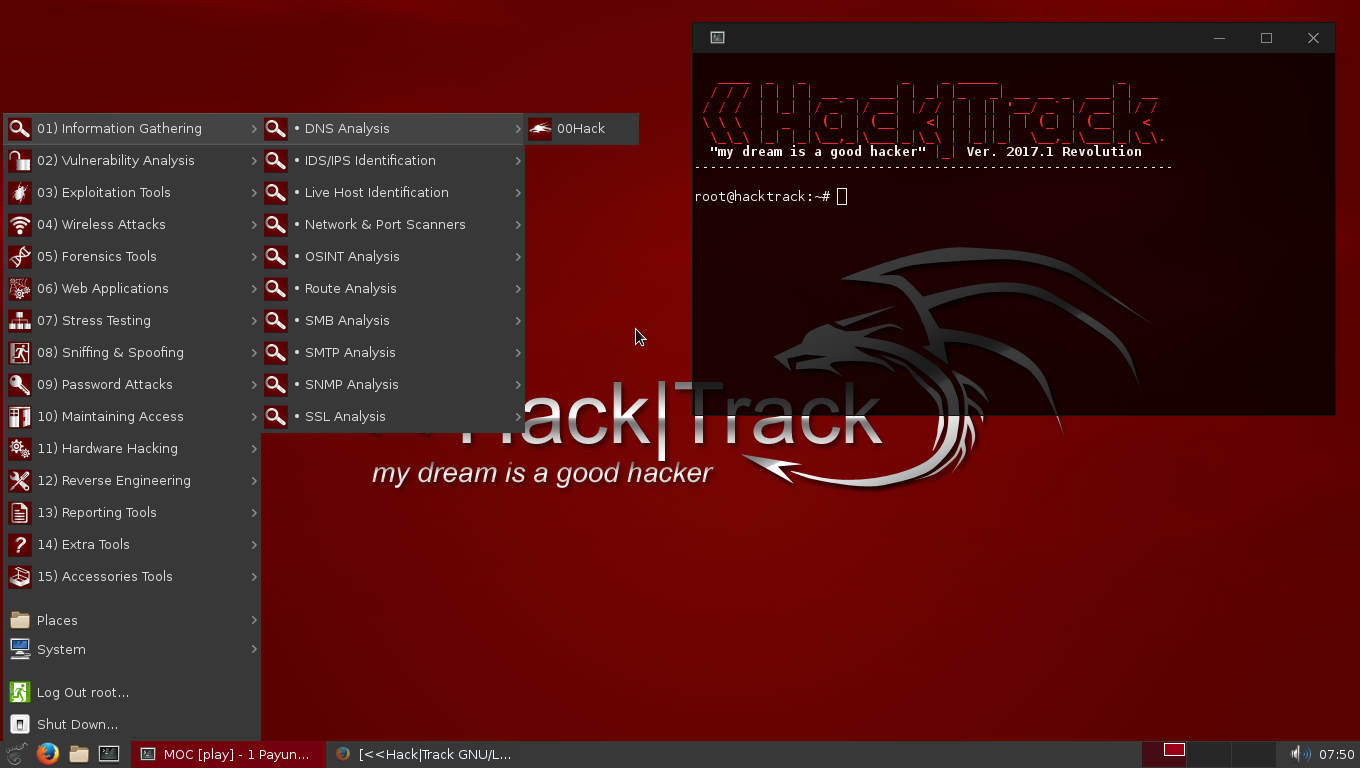
| Cb edits photoshop software download | Gruesome Grunts. HakTrak is a pioneer company in the region through its innovative-mindset, agile-approach, deep-experience, and project-delivery discipline. Designed for ethical hackers, bug bounty hunters, and small businesses, HackTrack provides structured, real-world plans to help you learn, execute, and document penetration tests effectively. She then starts to phase out and disappears into a Holo-Projector, revealing it is only a holographic clone of her. We protect people by securing organizations. Learn penetration testing with actionable steps tailored to real-world scenarios. Access plans created by experts and peers to broaden your learning experience. |
| Hacktrack | Mixtape creator |
| Hacktrack | Buku tutorial photoshop cs6 bahasa indonesia gratis download |
| Adobe photoshop 7 free download for windows 7 64 bit | 373 |
| Free download adobe acrobat reader | 170 |
| Roblox studio apk download android | Opener after effects template free download |
| Descargar acronis true image 2017 bootable usb | The monster snatches the device and teleports away. Bell - Mr. Born from the frustrations of chaotic pen-testing workflows, HackTrack exists to transform how cybersecurity is practiced. Hacktrack later returns and attacks the Rangers before he steals the Pink Ranger's Techno-Gadget that can "make the clones stronger. The operation dimension covers the necessary activities and steps required to execute the cybersecurity program effectively. Access plans created by experts and peers to broaden your learning experience. |



